Multiple subnets over the same VLAN interface
-
Hello experts,
I can't quite get my head around multiple subnets, so I hope if I describe in an example what's going on, someone might be able to point me in the right direction.
From a hosting company I get the following networks:
135.80.88.152/29 WAN interface IP
135.80.88.32/28 VLAN771
135.80.88.48/28 VLAN771The firewall is configured with:
135.80.88.154 on igb0
135.80.88.50 on igb0.771 (VLAN 771 defined on interface igb0)The question is how do I get the 135.80.88.32/28 onto the same interface? I can't create another VLAN with the same tag to create another interface and I can't add another network to the existing interface.
There are machines with IP out of both subnets behind the firewall and yes, they are public IP addresses so NAT shouldn't be an issue here I hope.
The same problem does exist for a private address space over a different VLAN, but essentially the same I get 2 subnets over the same VLAN provided by the hosting provider and there will be several machines behind the firewall in the private address space. This will require NAT translation outbound of course.
Cheers
Rob -
@wabbitde said in Multiple subnets over the same VLAN interface:
135.80.88.32/28 VLAN771
135.80.88.48/28 VLAN771
The firewall is configured with:
135.80.88.154 on igb0
135.80.88.50 on igb0.771 (VLAN 771 defined on interface igb0)
The question is how do I get the 135.80.88.32/28 onto the same interface?Just change the mask to /27.
@wabbitde said in Multiple subnets over the same VLAN interface:
There are machines with IP out of both subnets behind the firewall and yes, they are public IP addresses so NAT shouldn't be an issue here I hope.
You cannot have the same subnets on different interfaces. If the machines behind pfSense must have public IP addresses you have to bridge the external and internal interfaces.
-
@viragomann said in Multiple subnets over the same VLAN interface:
You cannot have the same subnets on different interfaces. If the machines behind pfSense must have public IP addresses you have to bridge the external and internal interfaces.
Or just have them route the /28s (They could both be summarized as 135.80.88.32/27) to 135.80.88.152 instead of doing that VLAN nonsense and you can do whatever you want with them.
-
@viragomann Thanks for the hint with /27. This may work on this one and seems just coincidence. This isn't always working with the other subnets.
-
@Derelict Yeah, I'm not sure that I'm in a position to tell IBM how to run their data centre networking. They've got thousands of customers sharing this, so their network has been thought through by many networking experts I'm sure.
-
If you want to route the subnets to something behind the firewall they need to be routed to you.
IBM should know this.
Perhaps you didn't choose the correct product based on the provisioning you require.
Did you even ask if they can be routed to you instead?
-
@wabbitde said in Multiple subnets over the same VLAN interface:
They've got thousands of customers sharing this, so their network has been thought through by many networking experts I'm sure.
You would think huh... But your not doing their cookie cutter setup where they directly attach shit to the netnwork, and not want to put stuff behind their own firewall.
For what your wanting to do routing the networks would be the better solution.. Just ask any networking expert..
-
Just create virtual IP addresses for the rest of the addresses and 1:1 NAT them.
-
Thanks @johnpoz and @Derelict .
Let's go back to the pfSense config for a minute. I've created a VLAN interface ix1.893 and assigned it an IP out of the 135.80.88.48/28 subnet.
The server behind the firewall has 135.80.88.47 and a VM running on the server has 135.80.88.53. The VM is in the same subnet has the OPT interface is configured and get's it's IP from the DHCP configured there. All good here. However, the physical host has an IP from the other subnet which is routed over the same VLAN. Assuming this is routed correctly to the device, what config do I need on the pfSense to make this go through? The pfSense has no IP assigned in that subnet and obviously the OPT interface can only have 1 IP address.
On the other firewall we have, we've simply assigned an IP address from the - let's call it VM network - to the physical host, thus the host and the VM's are in the same network on the OPT interface.
I'm just trying to understand if there is a config to make this work without changing the host to the VM network.
Thanks,
Rob -
You said you were going to NAT here:
This will require NAT translation outbound of course.
That is completely different than trying to put public addresses from the outside interfaces directly on hosts on the inside.
So what, exactly, are you trying to do?
One simple, hop-by-hop example would be best. A diagram might help. It's pretty difficult, for me at least, to cobble everything said there into something comprehensive.
-
Sorry, i tried to provide as much detail as possible, but maybe this was confusing:
Here is how (i think) it looks like. Let's focus on just the public IP addresses and forget NAT. The grey server (VM) will have a HTTP service listening on 135.80.88.53.
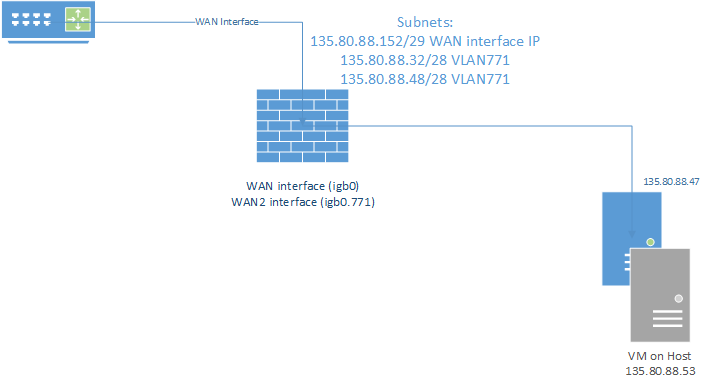 
It works to the extend that the VM get's it's IP from the DHCP. I can ping the VM from the pfSense Diagnostic/Ping. However, the host itself is not accessible, because it's in a different subnet.
For the full picture (eventually). The same happens on the private side. The private IP of the host is in a different subnet than the private IP of the VM on the host, but they come over the same VLAN.
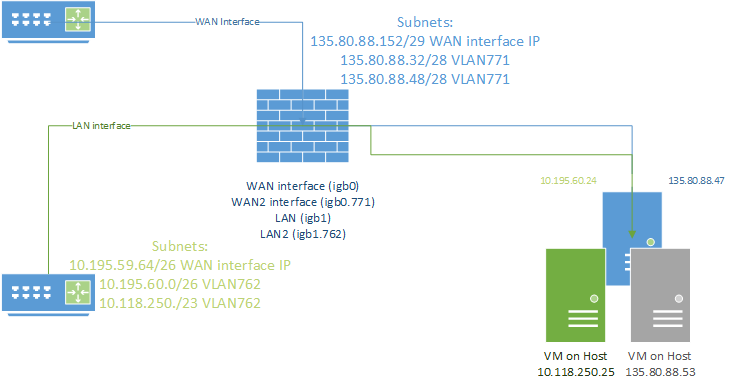
Let's forget outbound traffic and NAT for now. I'd be happy if the firewall can communicate with them at first.
-
You still did not provide one specific example demonstrating what is not working.
-
@Derelict I can't ping, RDP, anything, to the IP addresses of the host 135.80.88.47. The igb0.771 runs on 135.80.88.48/28. The firewall doesn't know about the 135.80.88.32/28 subnet.
-
Ping FROM WHERE?
-
From anywhere, home PC, office PC or the firewall itself. There are ANY rules in place for my home IP and the office IP before we get distracted by firewall rules. That's not the cause. I don't get log entries that it's being blocked.
VirtualIP's work for a single IP, e.g. i've got a secondary IP on the main WAN interface, but this doesn't seem to work with an entire subnet that easy. If I change the IP of the host to one within 135.80.88.48/28 I can RDP to it just fine, but this works just like any other interface and subnet and this will be my solution if I can't get the other subnet to work simultaneously.
-
How about a specific source IP address please?